The dystopian lake filled by the world’s tech lust
“Welcome to Baotou, the largest industrial city in Inner Mongolia. I’m here with a group of architects and designers called the Unknown Fields Division, and this is the final stop on a three-week-long journey up the global supply chain, tracing back the route consumer goods take from China to our shops and homes, via container ships and factories.
You may not have heard of Baotou, but the mines and factories here help to keep our modern lives ticking. It is one of the world’s biggest suppliers of “rare earth” minerals. These elements can be found in everything from magnets in wind turbines and electric car motors, to the electronic guts of smartphones and flatscreen TVs. In 2009 China produced 95% of the world’s supply of these elements, and it’s estimated that the Bayan Obo mines just north of Baotou contain 70% of the world’s reserves. But, as we would discover, at what cost?
After seeing the impact of rare earth mining myself, it’s impossible to view the gadgets I use everyday in the same way. As I watched Apple announce their smart watch recently, a thought crossed my mind: once we made watches with minerals mined from the Earth and treated them like precious heirlooms; now we use even rarer minerals and we’ll want to update them yearly. Technology companies continually urge us to upgrade; to buy the newest tablet or phone. But I cannot forget that it all begins in a place like Bautou, and a terrible toxic lake that stretches to the horizon.”




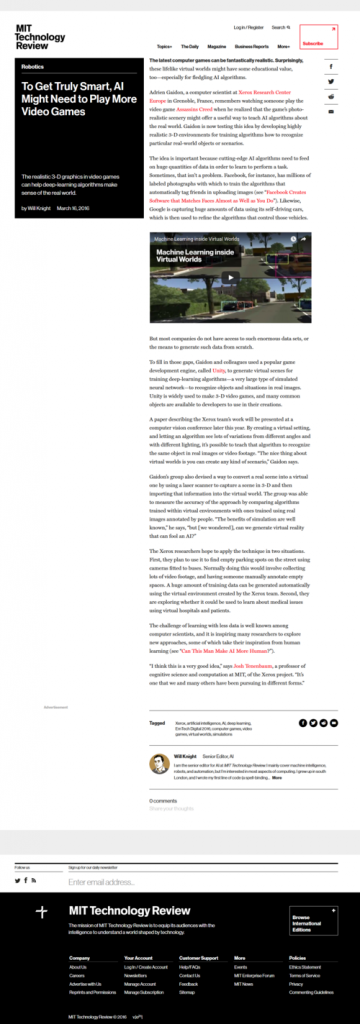 “The latest computer games can be fantastically realistic. Surprisingly, these lifelike virtual worlds might have some educational value, too—especially for fledgling AI algorithms.
“The latest computer games can be fantastically realistic. Surprisingly, these lifelike virtual worlds might have some educational value, too—especially for fledgling AI algorithms. For two weeks this past spring, some shoppers at the Westfield Stratford shopping mall in the United Kingdom were followed by a homeless dog appearing on electronic billboards. The roving canine, named Barley, was part of an RFID-based advertisement campaign conducted by Ogilvy on behalf of the Battersea Dogs and Cats Home, a rehabilitation and adoption organization for stray animals. The enabling technology was provided by Intellifi, and was installed by U.K.-based RFID consultancy RFIDiom.
For two weeks this past spring, some shoppers at the Westfield Stratford shopping mall in the United Kingdom were followed by a homeless dog appearing on electronic billboards. The roving canine, named Barley, was part of an RFID-based advertisement campaign conducted by Ogilvy on behalf of the Battersea Dogs and Cats Home, a rehabilitation and adoption organization for stray animals. The enabling technology was provided by Intellifi, and was installed by U.K.-based RFID consultancy RFIDiom.