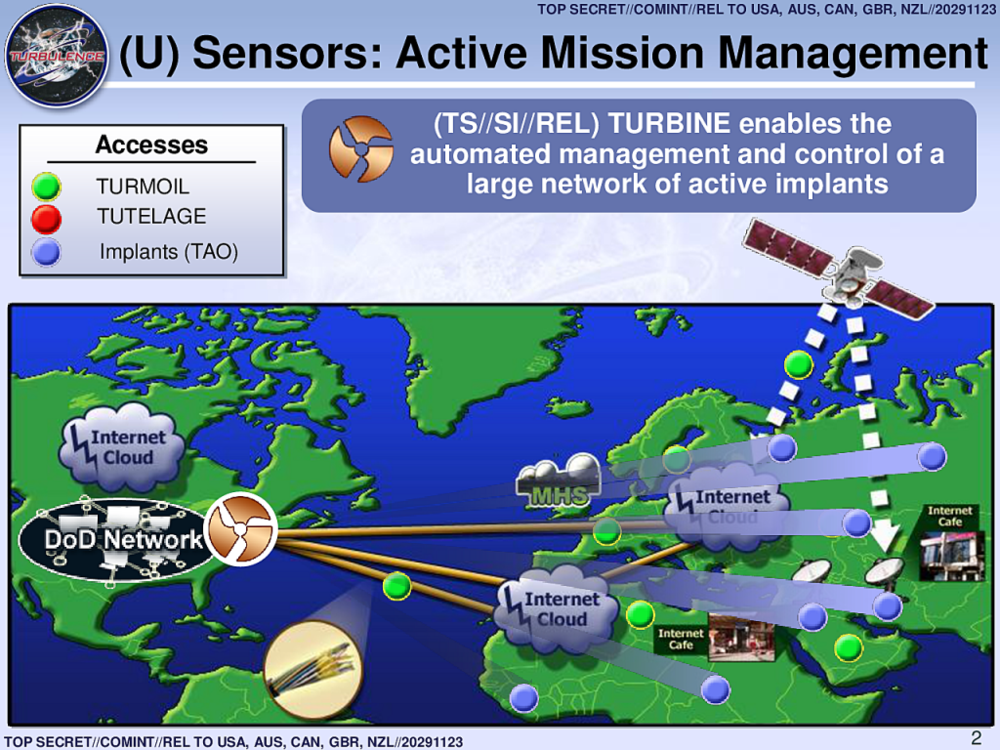
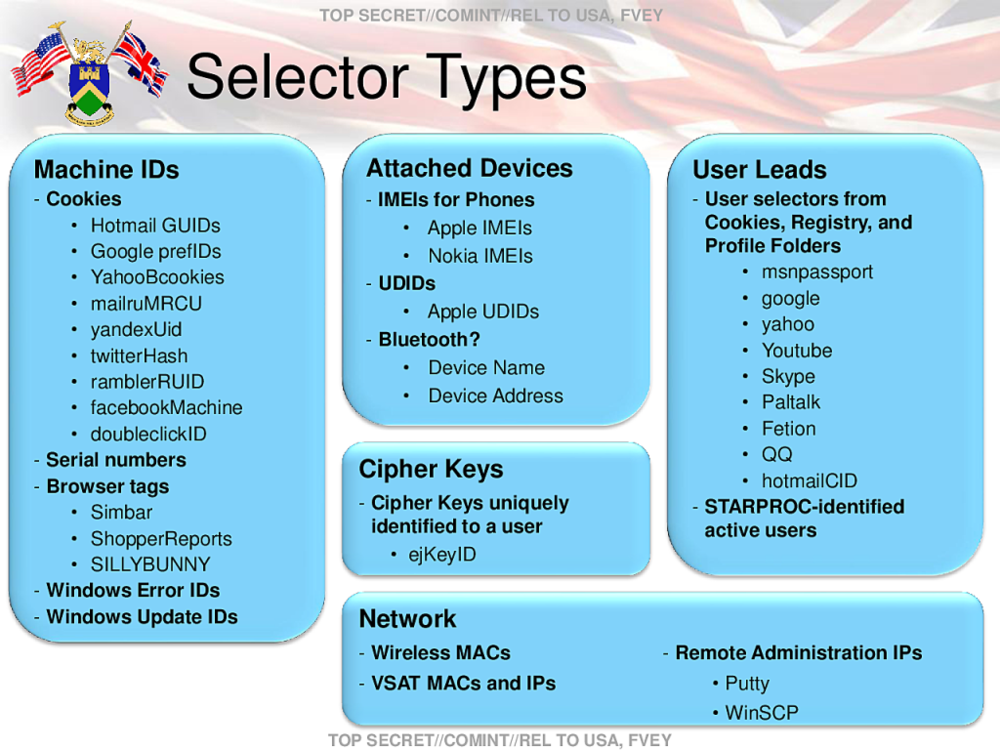
Ruin My Search History
Still using Google? Sick of them harvesting all your personal data and profiling you? Ruin My Search History is a simple tool that can help throw Google off the scent by generating random search queries. The tool prevents Google from building a more accurate picture of who you are by running random search queries in a small browser window. Decide just how random you want the searches to be using the slider and click ‘Ruin My Search History’.