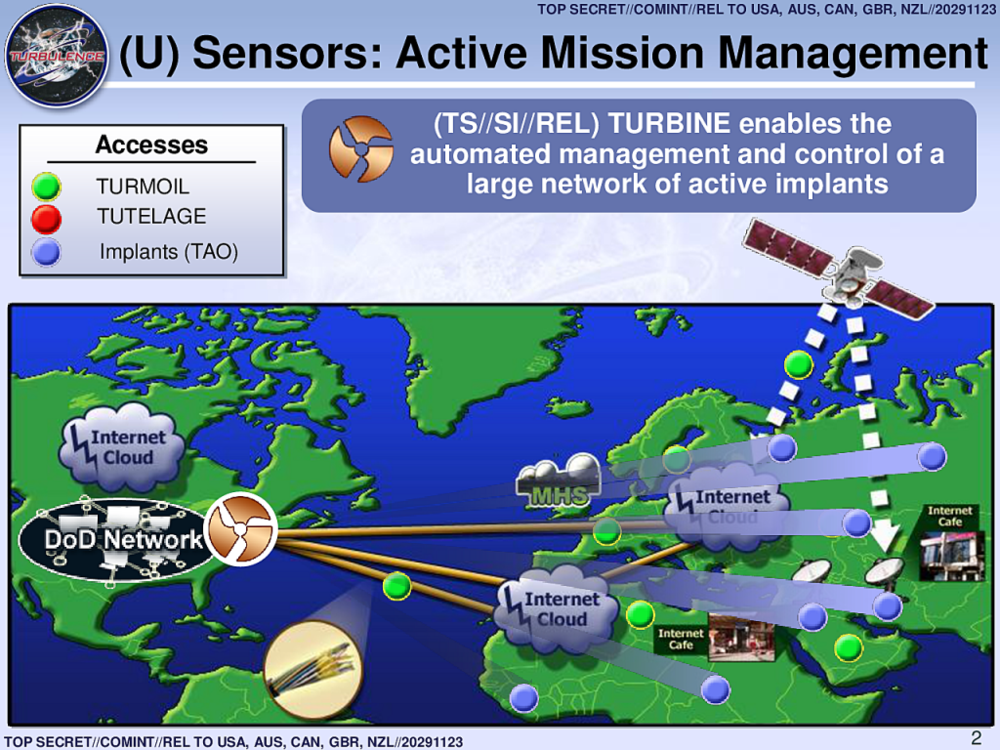
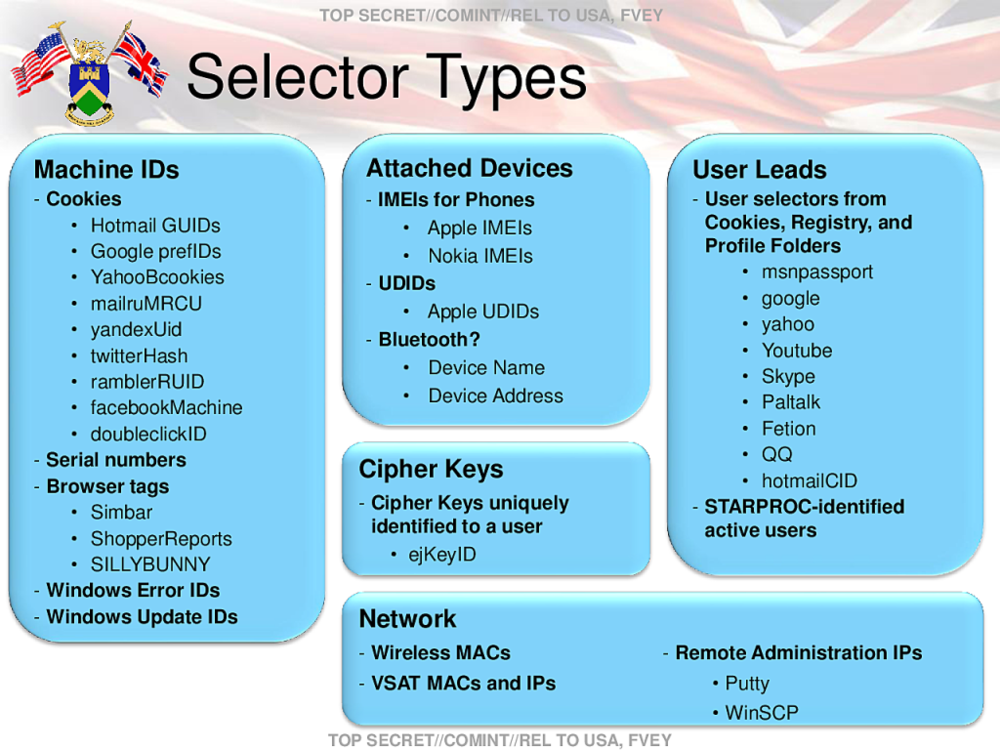
UK Spy Agency MI5 ‘Breached Surveillance Laws For More Than A Decade’
A UK tribunal has been told that security service MI5 has been breaching surveillance laws since 2010, and unlawfully obtaining bulk surveillance warrants against the public.
Human rights groups Liberty and Privacy International have told the Investigatory Powers Tribunal that MI5 has stored data on members of the public without the legal right to do so, and failed to disclose this to the Home Office and oversight bodies.
It breached safeguards around how long data was retained, who had access to it, and how legally privileged material such as private correspondence between lawyers and clients was protected, they say.
“MI5’s persistent failure to follow the law is inexcusable. For years, they have ignored safeguards put in place to protect us from abuse,” says Privacy International legal director Caroline Wilson Palow.
“These safeguards are a fundamental check on the vast power intelligence agencies can wield over all of us, especially when they engage in mass surveillance.”
The rights groups claim that the Home Office and various home secretaries failed to investigate these breaches. Surveillance warrants must be approved by the home secretary, who must be satisfied that legal safeguards around the handling of data are being met.
However, say Liberty and Privacy International, successive home secretaries repeatedly ignored the signs that MI5 was handling data unlawfully, and continued to sign off on surveillance warrants despite this.
“Surveillance safeguards can only protect us if they work in practice, and they don’t. For 10 years MI5 have been knowingly breaking the rules and failing to report it, and the government has failed to investigate clear red flags,” says Liberty lawyer Megan Goulding.
“There has been no proper investigation into MI5’s breaches by the Home Office, despite having been put on notice by briefings. Instead, the home secretary continued to issue unlawful warrants, and MI5 kept information from the authorities about how it mishandled our data.”
The allegations were first made in 2019 as part of Liberty’s separate legal challenge to the Investigatory Powers Act 2016, during which the government admitted that MI5 had been unlawfully retaining and mishandling the public’s data for years.
Documents shared with the court included correspondence between MI5 and its watchdog, the Investigatory Powers Commissioner’s Office (IPCO), as well as correspondence between MI5 and the Home Office, and reports of inspections carried out by IPCO after they learnt of MI5’s failings.
These documents revealed that MI5 itself called its data stores ‘ungoverned spaces’, and that the Investigatory Powers Commissioner had concluded MI5 had held and handled data in an ‘undoubted unlawful manner’.
“When we campaigned against giving the state unprecedented new surveillance powers under the so-called Snooper’s Charter back in 2015, one of our key concerns was that the safeguards against abuse were just not strong enough,” says Wilson Palow.
“And here we are, seven years later, with even the rules that are enshrined in law being ignored in practice. Those rules need a radical overhaul.”
Liberty and Privacy International have called for all surveillance warrants issued unlawfully to be quashed, all unlawfully retained data to be destroyed, and for the tribunal to declare that the Investigatory Powers Act itself is unlawful, because it doesn’t work in practice.

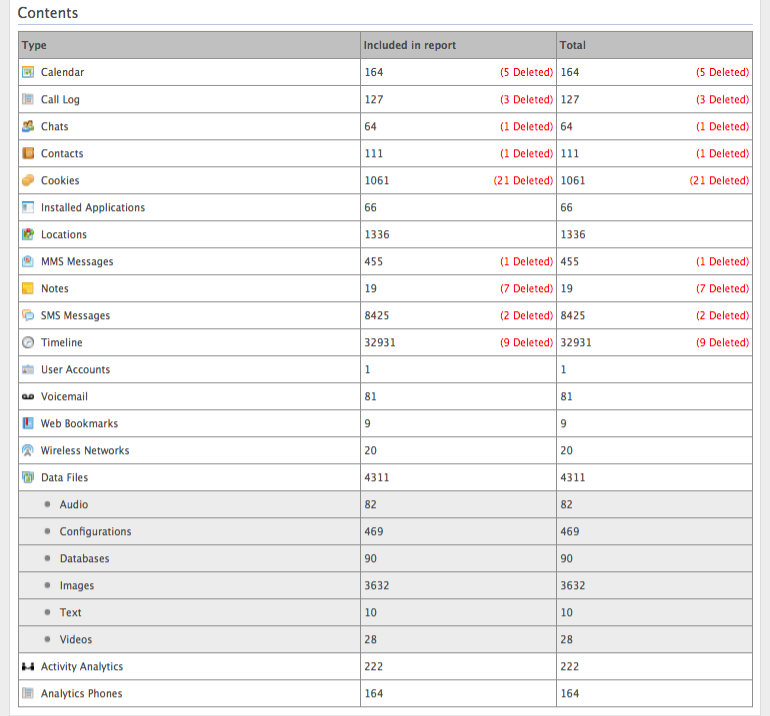

 “An inconspicuous Melbourne apartment block is home to a monitoring service that keeps watch on environment groups at the request of the federal government.
“An inconspicuous Melbourne apartment block is home to a monitoring service that keeps watch on environment groups at the request of the federal government.