China Debuts Anbot, the Police Robot


This study, that details the “Evolution of Wikipedia’s Norm Network,” could speak analogously to the supposed “democratisation” that technology pundits constantly invoke when idealising the web, not just in regards to Wikipedia, but even in more general terms about the Screen Culture. Also, mix in a reading of George Orwell’s ‘Animal Farm’ for good measure.
Emphasis added:
“Wikipedia is a voluntary organization dedicated to the noble goal of decentralized knowledge creation. But as the community has evolved over time, it has wandered further and further from its early egalitarian ideals, according to a new paper published in the journal Future Internet. In fact, such systems usually end up looking a lot like 20th-century bureaucracies. […] This may seem surprising, since there is no policing authority on Wikipedia — no established top-down means of control. The community is self-governing, relying primarily on social pressure to enforce the established core norms, according to co-author Simon DeDeo, a complexity scientist at Indiana University. […] “You start with a decentralized democratic system, but over time you get the emergence of a leadership class with privileged access to information and social networks,” DeDeo explained. “Their interests begin to diverge from the rest of the group. They no longer have the same needs and goals. So not only do they come to gain the most power within the system, but they may use it in ways that conflict with the needs of everybody else.”
“The general idea is to find datasets so enormous that they can reveal patterns invisible to conventional inquiry… But there’s a problem: It’s tempting to think that with such an incredible volume of data behind them, studies relying on big data couldn’t be wrong. But the bigness of the data can imbue the results with a false sense of certainty. Many of them are probably bogus — and the reasons why should give us pause about any research that blindly trusts big data.”
For example, Google’s database of scanned books represents 4% of all books ever published, but in this data set, “The Lord of the Rings gets no more influence than, say, Witchcraft Persecutions in Bavaria.” And the name Lanny appears to be one of the most common in early-20th century fiction — solely because Upton Sinclair published 11 different novels about a character named Lanny Budd.
The problem seems to be skewed data and misinterpretation. (The article points to the failure of Google Flu Trends, which it turns out “was largely predicting winter”.) The article’s conclusion? “Rather than succumb to ‘big data hubris,’ the rest of us would do well to keep our sceptic hats on — even when someone points to billions of words.”
“Alphabet’s [Google] executive chairman, Eric Schmidt, recently joined a Department of Defense advisory panel. Facebook recently hired a former director at the U.S. military’s research lab, Darpa. Uber employs Barack Obama’s former campaign manager David Plouffe and Amazon.com tapped his former spokesman Jay Carney. Google, Facebook, Uber and Apple collectively employ a couple of dozen former analysts for America’s spy agencies, who openly list their resumes on LinkedIn.
These connections are neither new nor secret. But the fact they are so accepted illustrates how tech’s leaders — even amid current fights over encryption and surveillance — are still seen as mostly U.S. firms that back up American values. Christopher Soghoian, a technologist with the American Civil Liberties Union, said low-level employees’ government connections matter less than leading executives’ ties to government. For instance, at least a dozen Google engineers have worked at the NSA, according to publicly available records on LinkedIn. And, this being Silicon Valley, not everyone who worked for a spy agency advertises that on LinkedIn. Soghoian, a vocal critic of mass surveillance, said Google hiring an ex-hacker for the NSA to work on security doesn’t really bother him. “But Eric Schmidt having a close relationship with the White House does…”
Emphasis added.
“Jason Bourne takes off his jacket, punches a man unconscious, looks forlornly off camera, and then a title card appears. The ad — five seconds of action — is a teaser for the full Jason Bourne trailer (video), which immediately follows the teaser. In fact, the micro-teaser and trailer are actually part of the same video, the former being an intro for the latter. The trend is the latest example of metahype, a marketing technique in which brands promote their advertisements as if they’re cultural events unto themselves.”
[…]“Last year, the studio advertised the teaser for Ant-Man with a ten-second cut of the footage reduced to an imperceptive scale. […] But where previous metahype promoted key dates in a marketing campaign—like official trailer releases and fan celebrations—the burgeoning trend of teasers within trailers exist purely to retain the viewer’s attention in that exact moment. The teaser within the trailer speaks to a moment in which we have so many distractions and choices that marketers must sell us on giving a trailer three minutes of our time. This practice isn’t limited to movie trailers, though. Next time you’re on Facebook, pay attention to how the popular videos in your newsfeed are edited. Is the most interesting image the first thing you see? And does that trick get you to stop scrolling and watch?”
UK’s intelligence agencies such as MI5, MI6, and GCHQ have been collecting personal information from citizens who are “unlikely to be of intelligence or security interest” since the 1990s, previously confidential documents reveal. The documents were published as a result of a lawsuit filed by Privacy International, and according to the files, GCHQ and others have been collecting bulk personal data sets since 1998.
Emphasis added:
“These records can be “anything from your private medical records, your correspondence with your doctor or lawyer, even what petitions you have signed, your financial data, and commercial activities,” Privacy International legal officer Millie Graham Wood said in a statement. “The information revealed by this disclosure shows the staggering extent to which the intelligence agencies hoover up our data.”
Nor, it seems, are BPDs only being used to investigate terrorism and serious crime; they can and are used to protect Britain’s “economic well-being”—including preventing pirate copies of Harry Potter books from leaking before their release date.
BPDs are so powerful, in fact, that the normally toothless UK parliament watchdog that oversees intelligence gathering, the Intelligence and Security Committee (ISC), recommended in February that “Class Bulk Personal Dataset warrants are removed from the new legislation.”
These data sets are so large and collect so much information so indiscriminately that they even include information on dead people.”
The Intercept has obtained a secret, internal U.S. government catalogue of dozens of cellphone surveillance devices used by the military and by intelligence agencies. The document, thick with previously undisclosed information, also offers rare insight into the spying capabilities of federal law enforcement and local police inside the United States.
The catalogue includes details on the Stingray, a well-known brand of surveillance gear, as well as Boeing “dirt boxes” and dozens of more obscure devices that can be mounted on vehicles, drones, and piloted aircraft. Some are designed to be used at static locations, while others can be discreetly carried by an individual. They have names like Cyberhawk, Yellowstone, Blackfin, Maximus, Cyclone, and Spartacus. Within the catalogue, the NSA is listed as the vendor of one device, while another was developed for use by the CIA, and another was developed for a special forces requirement. Nearly a third of the entries focus on equipment that seems to have never been described in public before.
Slides of the catalogue available here, while a stylised version is available here.
“Welcome to Baotou, the largest industrial city in Inner Mongolia. I’m here with a group of architects and designers called the Unknown Fields Division, and this is the final stop on a three-week-long journey up the global supply chain, tracing back the route consumer goods take from China to our shops and homes, via container ships and factories.
You may not have heard of Baotou, but the mines and factories here help to keep our modern lives ticking. It is one of the world’s biggest suppliers of “rare earth” minerals. These elements can be found in everything from magnets in wind turbines and electric car motors, to the electronic guts of smartphones and flatscreen TVs. In 2009 China produced 95% of the world’s supply of these elements, and it’s estimated that the Bayan Obo mines just north of Baotou contain 70% of the world’s reserves. But, as we would discover, at what cost?
After seeing the impact of rare earth mining myself, it’s impossible to view the gadgets I use everyday in the same way. As I watched Apple announce their smart watch recently, a thought crossed my mind: once we made watches with minerals mined from the Earth and treated them like precious heirlooms; now we use even rarer minerals and we’ll want to update them yearly. Technology companies continually urge us to upgrade; to buy the newest tablet or phone. But I cannot forget that it all begins in a place like Bautou, and a terrible toxic lake that stretches to the horizon.”
Emphasis added:
“There are many other examples of intelligent technology gone bad, but more often than not they involve deception rather than physical danger. Malevolent bots, designed by criminals, are now ubiquitous on social media sites and elsewhere online. The mobile dating app Tinder, for example, has been frequently infiltrated by bots posing as real people that attempt to manipulate users into using their webcams or disclosing credit card information. So it’s not a stretch to imagine that untrustworthy bots may soon come to the physical world.
Meanwhile, increasing evidence suggests that we are susceptible to telling our deepest, darkest secrets to anthropomorphic robots whose cute faces may hide exploitative code – children particularly so. So how do we protect ourselves from double-crossing decepticons?”
“UC Literature Professor Jackson Bliss puts into words something many of you have probably experienced: the evolution of the internet and mobile devices has changed how we read. “The truth is that most of us read continuously in a perpetual stream of incestuous words, but instead of reading novels, book reviews, or newspapers like we used to in the ancien régime, we now read text messages, social media, and bite-sized entries about our protean cultural history on Wikipedia.”
Bliss continues, “In the great epistemic galaxy of words, we have become both reading junkies and also professional text skimmers. … Reading has become a relentless exercise in self-validation, which is why we get impatient when writers don’t come out and simply tell us what they’re arguing. … Content—whether thought-provoking, regurgitated, or analytically superficial, impeccably-researched, politically doctrinaire, or grammatically atrocious—now occupies the same cultural space, the same screen space, and the same mental space in the public imagination. After awhile, we just stop keeping track of what’s legitimately good because it takes too much energy to separate the crème from the foam.”
“Security researcher Mike Olsen has warned that some products sold through the Amazon marketplace are habouring a dark secret — malware.
Olsen said in a blog post that while scouring Amazon for a decent set of outdoor surveillance cameras for a friend, he came across a deal for 6 PoE cameras and recording equipment.
The seller, Urban Security Group, had generally good reviews and was offering a particular Sony setup on sale.
After purchasing the kit, Olsen started setting up the surveillance system, logging into the administrator panel to configure it.
While the page hosted the camera feed, no “normal controls or settings were available,” according to the researcher.
”Being one of those guys who assumes bad CSS, I went ahead and opened up developer tools,” Olsen said.
”Maybe a bad style was hiding the options I needed. Instead what I found tucked at the bottom of the body tag was an iframe linking to a very strange looking host name.”
Further investigation revealed the host name, Brenz.pl, is linked to malware distribution.
According to cybersecurity firm Securi, Brenz was first spotted distributing malware back in 2009 before being shut down, but reemerged in 2011. Compromised domains link to the address through malicious iFrames for the purpose of distributing malware hosted on the website.
VirusTotal recognizes the web domain as a malicious source and scans reveal that Trojans and viruses may be hosted by Brenz.pl.
If the device’s firmware links to this domain, malware can be downloaded and installed, potentially leading to unlawful surveillance and data theft.
The problem was also recently brought up in a forum post on the SC10IP firmware, which is used in commercial products and also links to Brenz.pl.
Threats do not just come from dodgy social media links, phishing campaigns or social engineering — firmware can host malware, too.
The take-home from this is that any device, especially when it contains networking or Internet capabilities, can harbour threats to personal safety and data security, and while the average person is unlikely to do a full-scale code search, checking reviews and alerts for such products online is worthwhile — even if the platform is trusted.
”Amazon stuff can contain malware,” Olsen said.”
“A new study shows that knowledge of government surveillance causes people to self-censor their dissenting opinions online. The research offers a sobering look at the oft-touted “democratizing” effect of social media and Internet access that bolsters minority opinion.
The study, published in Journalism and Mass Communication Quarterly, studied the effects of subtle reminders of mass surveillance on its subjects. The majority of participants reacted by suppressing opinions that they perceived to be in the minority. This research illustrates the silencing effect of participants’ dissenting opinions in the wake of widespread knowledge of government surveillance, as revealed by whistleblower Edward Snowden in 2013.
The “spiral of silence” is a well-researched phenomenon in which people suppress unpopular opinions to fit in and avoid social isolation. It has been looked at in the context of social media and the echo-chamber effect, in which we tailor our opinions to fit the online activity of our Facebook and Twitter friends. But this study adds a new layer by explicitly examining how government surveillance affects self-censorship.”
“The more time young adults spend on social media, the more likely they are to become depressed, a study has found.
Of the 19 to 32-year-olds who took part in the research, those who checked social media most frequently throughout the week were 2.7 times more likely to develop depression than those who checked least often.
The 1,787 US participants used social media for an average 61 minutes every day, visiting accounts 30 times per week. Of them a quarter were found to have high indicators of depression.”
“Starting this summer, the [Japanese] government will test a system in which foreign tourists will be able to verify their identities and buy things at stores using only their fingerprints.
The government hopes to increase the number of foreign tourists by using the system to prevent crime and relieve users from the necessity of carrying cash or credit cards. It aims to realize the system by the 2020 Tokyo Olympic and Paralympic Games.
The experiment will have inbound tourists register their fingerprints and other data, such as credit card information, at airports and elsewhere.
Tourists would then be able to conduct tax exemption procedures and make purchases after verifying their identities by placing two fingers on special devices installed at stores.”
“Tomorrow marks the 35th anniversary of Food Not Bombs—the name given to autonomous groups and independent collectives that serve free vegan and vegetarian food in opposition of poverty and hunger, and also in protest of economic disparity and rapacious militarism. But, “despite seemingly the non-controversial nature of the activist group’s titular three-word mission statement, FBI files released earlier this week show that serving up home-cooked vegan moussaka is apparently enough to warrant suspicions of terrorism.
The files, which begin in the early naughts, appear to be focused on one particular FNB chapter based out of Virginia Commonwealth University in Richmond, Virginia. The bulk of the records concern the organization’s rather obvious opposition to the Iraq war.
In fact, the release included a CD comprised of extensive surveillance footage from an anti-war protest in Richmond on July 3rd, 2003.”
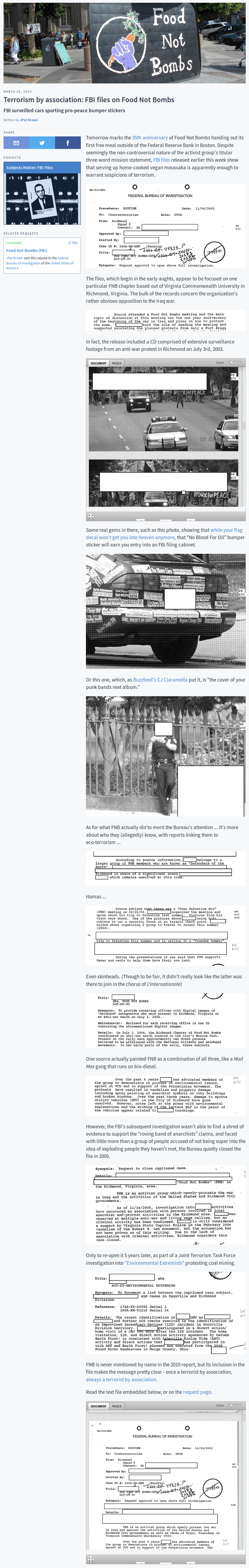
“Soft robots that can grasp delicate objects, computer algorithms designed to spot an “insider threat,” and artificial intelligence that will sift through large data sets — these are just a few of the technologies being pursued by companies with investment from In-Q-Tel, the CIA’s venture capital firm, according to a document obtained by The Intercept.
Yet among the 38 previously undisclosed companies receiving In-Q-Tel funding, the research focus that stands out is social media mining and surveillance; the portfolio document lists several tech companies pursuing work in this area, including Dataminr, Geofeedia, PATHAR, and TransVoyant.”
Source: https://theintercept.com/2016/04/14/in-undisclosed-cia-investments-social-media-mining-looms-large/
And…
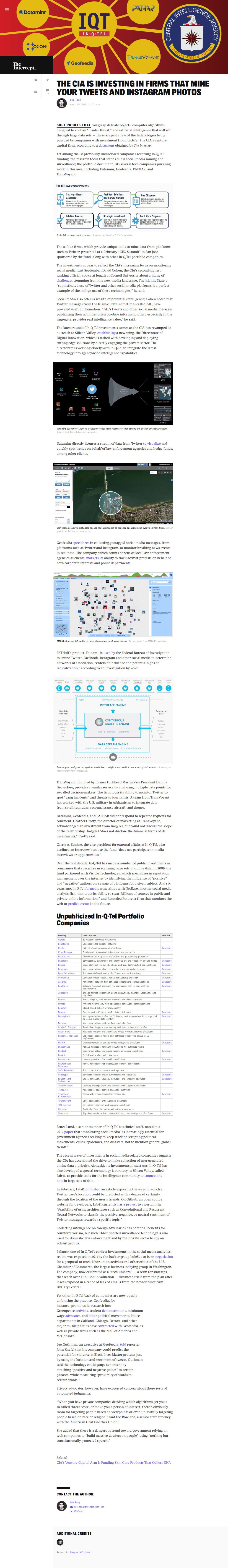
“SKINCENTIAL SCIENCES, a company with an innovative line of cosmetic products marketed as a way to erase blemishes and soften skin, has caught the attention of beauty bloggers on YouTube, Oprah’s lifestyle magazine, and celebrity skin care professionals. Documents obtained by The Intercept reveal that the firm has also attracted interest and funding from In-Q-Tel, the venture capital arm of the Central Intelligence Agency.
The previously undisclosed relationship with the CIA might come as some surprise to a visitor to the website of Clearista, the main product line of Skincential Sciences, which boasts of a “formula so you can feel confident and beautiful in your skin’s most natural state.”
Though the public-facing side of the company touts a range of skin care products, Skincential Sciences developed a patented technology that removes a thin outer layer of the skin, revealing unique biomarkers that can be used for a variety of diagnostic tests, including DNA collection.
Skincential Science’s noninvasive procedure, described on the Clearista website as “painless,” is said to require only water, a special detergent, and a few brushes against the skin, making it a convenient option for restoring the glow of a youthful complexion — and a novel technique for gathering information about a person’s biochemistry.”
Source: https://theintercept.com/2016/04/08/cia-skincare-startup/
“Tinder isn’t as private as many of its users think, and a new website which aims to exploit that is causing concern among users of the dating app.
“Swipebuster” promises to let Tinder users find out whether people they know have an account on the dating app, and even stalk them down to their last known location.
The website charges $4.99 (£3.50) to let someone see whether the target is using Tinder, and can narrow down results by first name, age, gender and location.
But it doesn’t do so by hacking into Tinder, or even by “scraping” the app manually. Instead, it searches the database using Tinder’s official API, which is intended for use by third-party developers who want to write software that plugs in with the site. All the information that it can reveal is considered public by the company, and revealed through the API with few safeguards.
Although the site seems targeted at those who want to catch cheating partners on the app, its developer says he had a different motivation in mind, telling Vanity Fair that he wanted to highlight oversharing online.
“There is too much data about people that people themselves don’t know is available,” the anonymous developer said. “Not only are people oversharing and putting out a lot of information about themselves, but companies are also not doing enough to let people know they’re doing it.”
But the argument that Swipebuster is made to highlight privacy breaches on Tinder’s part seems questionable when one looks at the website itself. Under a headline reading “Find out if they’re using Tinder for only $4.99”, the site says nothing about privacy or expectations thereof, instead offering only a walkthrough for users who want to pay for its services. An animated gif showing the process ends with an image of the supposed target superimposed with the word “Busted”.
Still using Google? Sick of them harvesting all your personal data and profiling you? Ruin My Search History is a simple tool that can help throw Google off the scent by generating random search queries. The tool prevents Google from building a more accurate picture of who you are by running random search queries in a small browser window. Decide just how random you want the searches to be using the slider and click ‘Ruin My Search History’.