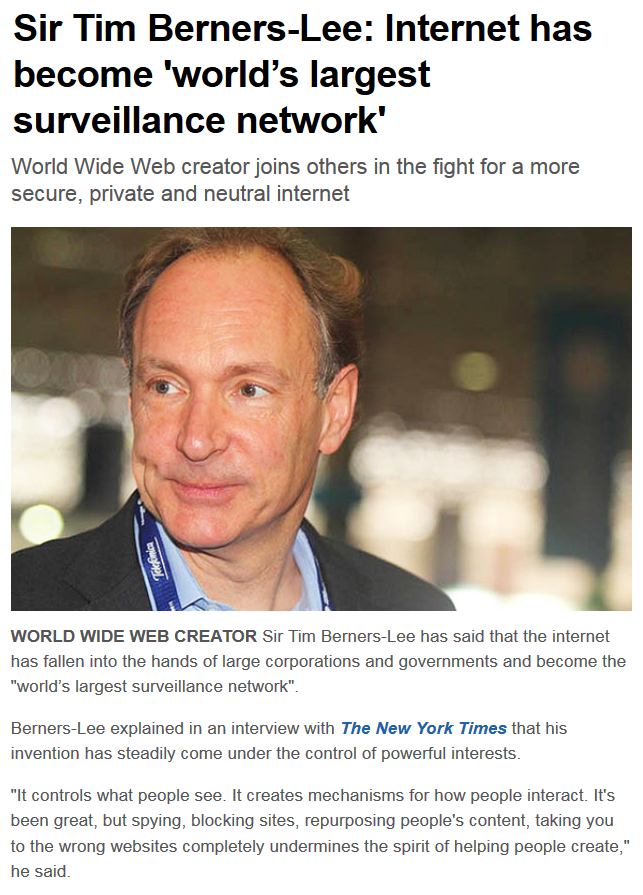
How technology disrupted the truth
Coinciding with a continued rise in public cynicism and a legitimate mistrust of mainstream media beholden to systems of power that are discredited, it seems most people turn to social media networks to get their news now. But this seemingly doesn’t fix the problem. Rather than a “democratisation” of the media and/or a mass reclamation of investigative journalism (as technology pundits continuously purport), there’s arguably been the opposite.
Now, with the convergence of closed social media networks that are beholden to nefarious algorithms such as The Filter Bubble and the personalisation of information, as an article in the Guardian explains, “Social media has swallowed the news – threatening the funding of public-interest reporting and ushering in an era when everyone has their own facts. But the consequences go far beyond journalism.”
“Twenty-five years after the first website went online, it is clear that we are living through a period of dizzying transition. For 500 years after Gutenberg, the dominant form of information was the printed page: knowledge was primarily delivered in a fixed format, one that encouraged readers to believe in stable and settled truths.
Now, we are caught in a series of confusing battles between opposing forces: between truth and falsehood, fact and rumour, kindness and cruelty; between the few and the many, the connected and the alienated; between the open platform of the web as its architects envisioned it and the gated enclosures of Facebook and other social networks; between an informed public and a misguided mob.
What is common to these struggles – and what makes their resolution an urgent matter – is that they all involve the diminishing status of truth. This does not mean that there are no truths. It simply means, as this year has made very clear, that we cannot agree on what those truths are, and when there is no consensus about the truth and no way to achieve it, chaos soon follows.
Increasingly, what counts as a fact is merely a view that someone feels to be true – and technology has made it very easy for these “facts” to circulate with a speed and reach that was unimaginable in the Gutenberg era (or even a decade ago).
Too much of the press often exhibited a bias towards the status quo and a deference to authority, and it was prohibitively difficult for ordinary people to challenge the power of the press. Now, people distrust much of what is presented as fact – particularly if the facts in question are uncomfortable, or out of sync with their own views – and while some of that distrust is misplaced, some of it is not.
In the digital age, it is easier than ever to publish false information, which is quickly shared and taken to be true – as we often see in emergency situations, when news is breaking in real time.”
It’s like the well-oiled tactics of the tobacco industry that have since permeated pretty much all industries—confuse the hell out of people so they don’t know what’s true anymore. It’s a popular PR tactic honed over decades for social control and manipulation of democracy, and it’s that element that exists and is especially reinforced online (particularly in real time), in the giant echo chamber of corporate social media networks, where the user is constantly subjected to streams and streams of information about current events—most devoid of context, analysis, or even significant depth in the time and space of a tweet.
The grounding that gives rise to physical reality and epistemological truths goes missing when we’re tied to screens that simply reflect our projections.
In the words of Sherry Turkle, the issues facing our planet right now cannot be solved in the time-space of texting/tweeting. So if the way we understand, perceive and relate to the world through the prism of media (mainstream media and social media alike) is in decline, it should tell us volumes about the state of democracy…
Global Voices’ adds: “The need for fact-checking hasn’t gone away. As new technologies have spawned new forms of media which lend themselves to the spread of various kinds of disinformation, this need has in fact grown. Much of the information that’s spread online, even by news outlets, is not checked, as outlets simply copy-paste — or in some instances, plagiarise — “click-worthy” content generated by others. Politicians, especially populists prone to manipulative tactics, have embraced this new media environment by making alliances with tabloid tycoons or by becoming media owners themselves.
UPDATE 29/7 — Example, of sorts. “#SaveMarinaJoyce conspiracy theories about British YouTuber go viral.” News reporting social media rumours, facts from source ignite disbelief and cynicism, confirmation bias at work, etc.


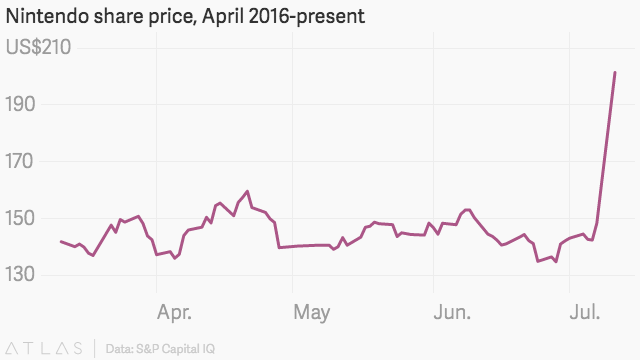
 The app’s popularity has created lagging servers and forced the company Niantic to delay its international roll-out, meaning “Those who have already downloaded the game in the U.S., Australia and New Zealand can still play it, while those in the U.K., the Netherlands and other countries will have to wait.”
The app’s popularity has created lagging servers and forced the company Niantic to delay its international roll-out, meaning “Those who have already downloaded the game in the U.S., Australia and New Zealand can still play it, while those in the U.K., the Netherlands and other countries will have to wait.”