How mass surveillance silences minority opinions
“A new study shows that knowledge of government surveillance causes people to self-censor their dissenting opinions online. The research offers a sobering look at the oft-touted “democratizing” effect of social media and Internet access that bolsters minority opinion.
The study, published in Journalism and Mass Communication Quarterly, studied the effects of subtle reminders of mass surveillance on its subjects. The majority of participants reacted by suppressing opinions that they perceived to be in the minority. This research illustrates the silencing effect of participants’ dissenting opinions in the wake of widespread knowledge of government surveillance, as revealed by whistleblower Edward Snowden in 2013.
The “spiral of silence” is a well-researched phenomenon in which people suppress unpopular opinions to fit in and avoid social isolation. It has been looked at in the context of social media and the echo-chamber effect, in which we tailor our opinions to fit the online activity of our Facebook and Twitter friends. But this study adds a new layer by explicitly examining how government surveillance affects self-censorship.”



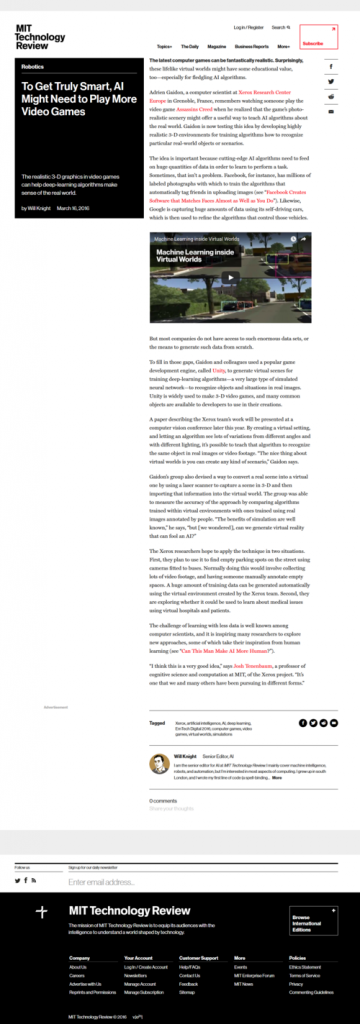 “The latest computer games can be fantastically realistic. Surprisingly, these lifelike virtual worlds might have some educational value, too—especially for fledgling AI algorithms.
“The latest computer games can be fantastically realistic. Surprisingly, these lifelike virtual worlds might have some educational value, too—especially for fledgling AI algorithms. For two weeks this past spring, some shoppers at the Westfield Stratford shopping mall in the United Kingdom were followed by a homeless dog appearing on electronic billboards. The roving canine, named Barley, was part of an RFID-based advertisement campaign conducted by Ogilvy on behalf of the Battersea Dogs and Cats Home, a rehabilitation and adoption organization for stray animals. The enabling technology was provided by Intellifi, and was installed by U.K.-based RFID consultancy RFIDiom.
For two weeks this past spring, some shoppers at the Westfield Stratford shopping mall in the United Kingdom were followed by a homeless dog appearing on electronic billboards. The roving canine, named Barley, was part of an RFID-based advertisement campaign conducted by Ogilvy on behalf of the Battersea Dogs and Cats Home, a rehabilitation and adoption organization for stray animals. The enabling technology was provided by Intellifi, and was installed by U.K.-based RFID consultancy RFIDiom.


 “An inconspicuous Melbourne apartment block is home to a monitoring service that keeps watch on environment groups at the request of the federal government.
“An inconspicuous Melbourne apartment block is home to a monitoring service that keeps watch on environment groups at the request of the federal government.