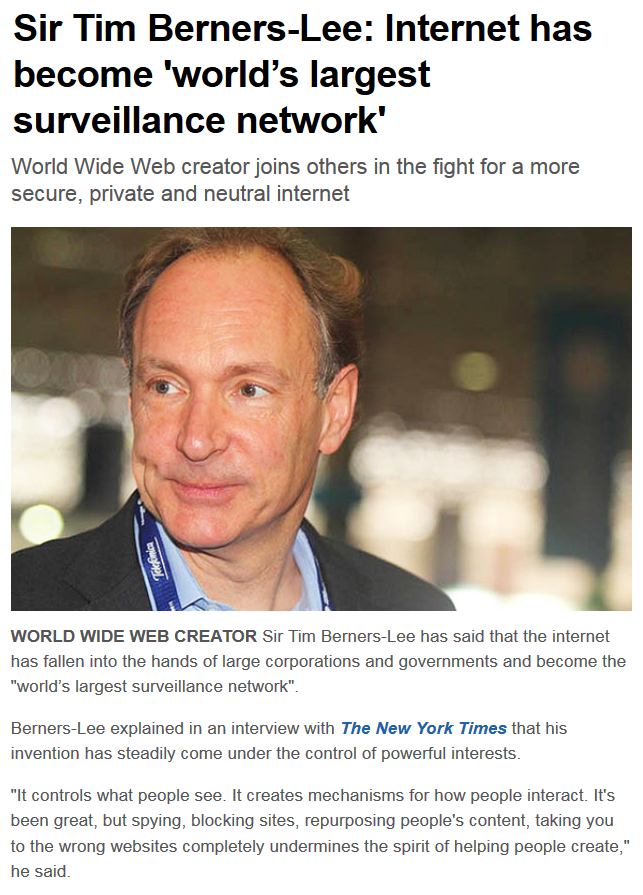
WWW Inventor Tim Berners-Lee says, “the Internet has become the world’s largest surveillance network.”
“Tim Berners-Lee has said that the internet has fallen into the hands of large corporations and governments and become the “world’s largest surveillance network”.
Berners-Lee explained in an interview with The New York Times that his invention has steadily come under the control of powerful interests.
“It controls what people see. It creates mechanisms for how people interact. It’s been great, but spying, blocking sites, repurposing people’s content, taking you to the wrong websites completely undermines the spirit of helping people create,” he said.”



 “An inconspicuous Melbourne apartment block is home to a monitoring service that keeps watch on environment groups at the request of the federal government.
“An inconspicuous Melbourne apartment block is home to a monitoring service that keeps watch on environment groups at the request of the federal government.