Digital Disconnect: How Capitalism is Turning the Internet Against Democracy
Robert McChesney (2014)
 Celebrants and skeptics alike have produced valuable analyses of the Internet’s effect on us and our world, oscillating between utopian bliss and dystopian hell. But according to Robert W. McChesney, arguments on both sides fail to address the relationship between economic power and the Internet.
Celebrants and skeptics alike have produced valuable analyses of the Internet’s effect on us and our world, oscillating between utopian bliss and dystopian hell. But according to Robert W. McChesney, arguments on both sides fail to address the relationship between economic power and the Internet.
McChesney’s award-winning Rich Media, Poor Democracy skewered the assumption that a society drenched in commercial information is a democratic one. In Digital Disconnect, McChesney returns to this provocative thesis in light of the advances of the digital age. He argues that the sharp decline in the enforcement of antitrust violations, the increase in patents on digital technology and proprietary systems and massive indirect subsidies and other policies have made the internet a place of numbing commercialism. A handful of monopolies now dominate the political economy, from Google, which garners a 97 percent share of the mobile search market, to Microsoft, whose operating system is used by over 90 percent of the world’s computers.
Capitalism’s colonization of the Internet has spurred the collapse of credible journalism and made the internet an unparalleled apparatus for government and corporate surveillance and a disturbingly antidemocratic force.
In Digital Disconnect, Robert McChesney offers a groundbreaking critique of the Internet, urging us to reclaim the democratizing potential of the digital revolution while we still can.

 We live in a world unimaginable only decades ago: a domain of backlit screens, instant information, and vibrant experiences that can outcompete dreary reality. Our brave new technologies offer incredible opportunities for work and play. But at what price?
We live in a world unimaginable only decades ago: a domain of backlit screens, instant information, and vibrant experiences that can outcompete dreary reality. Our brave new technologies offer incredible opportunities for work and play. But at what price?

 “Now that communication can be as quick as thought, why hasn’t our ability to organize politically—to establish gains and beyond that, to maintain them—kept pace? The web has given us both capacity and speed: but progressive change seems to be something perpetually in the air, rarely manifesting, even more rarely staying with us.
“Now that communication can be as quick as thought, why hasn’t our ability to organize politically—to establish gains and beyond that, to maintain them—kept pace? The web has given us both capacity and speed: but progressive change seems to be something perpetually in the air, rarely manifesting, even more rarely staying with us.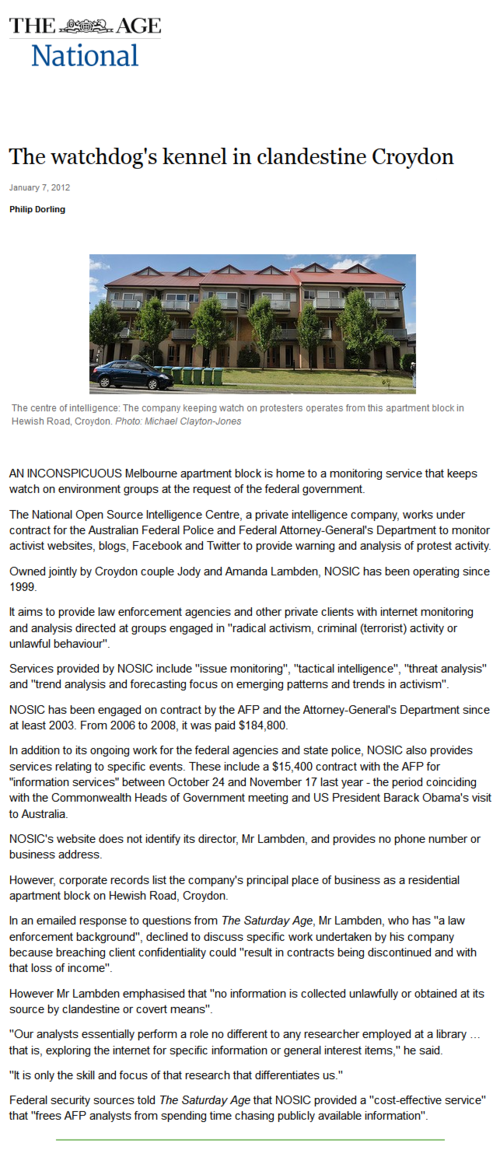 “An inconspicuous Melbourne apartment block is home to a monitoring service that keeps watch on environment groups at the request of the federal government.
“An inconspicuous Melbourne apartment block is home to a monitoring service that keeps watch on environment groups at the request of the federal government.

