Gen Z rely on social media as their main news source
Over half of Australians (51%) access news more than once a day, which is a 3 percentage point increase from last year.
Almost half of Australians (49%) use social media to access news, marking a 4 percentage point increase since last year. Nearly two-thirds of Gen Z (60%) rely on social media as their main news source, which is a significant increase of 17 percentage points in the past year.
Trust in news generally fell slightly (-3pp) to 40% but remains within the long-term trend of trust hovering in the low 40s. However, distrust is rising consistently and at a faster rate than trust in news is falling. Distrust is at its highest point since 2016 (33% +8pp).
News avoidance remains high (68%) and close to the global average.
Since 2019 there has been a 13 percentage point increase in those saying they are worn out by the volume of news. News fatigue is prevalent among light news consumers and social media news users.
Over the past two years, podcast listening has increased among Gen Z women to 61% (+14pp) and Baby Boomers+ to 18% (+4pp). In general, men (44%) are still more likely than women (35%) to have listened to a podcast in the last month.
Reflecting the growth of TikTok and Instagram Reels, video news consumption is becoming increasingly popular, especially short form news videos.

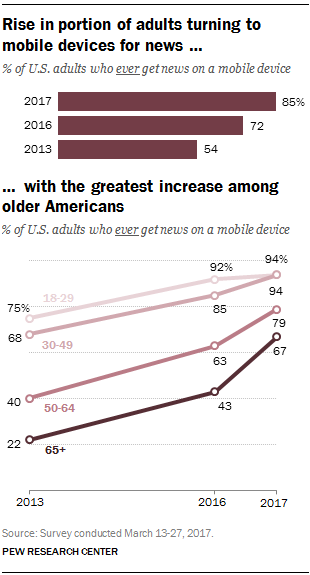 Mobile devices have rapidly become one of the most common ways for Americans to get news, and the sharpest growth in the past year has been among Americans ages 50 and older, according to a
Mobile devices have rapidly become one of the most common ways for Americans to get news, and the sharpest growth in the past year has been among Americans ages 50 and older, according to a