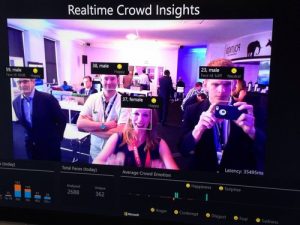
Baltimore Police took one million surveillance photos of city with secret plane
“Baltimore Police on Friday released data showing that a surveillance plane secretly flew over the city roughly 100 times, taking more than 1 million snapshots of the streets below.
Police held a news conference where they released logs tracking flights of the plane owned and operated by Persistent Surveillance Systems, which is promoting the aerial technology as a cutting-edge crime-fighting tool.
The logs show the plane spent about 314 hours over eight months creating the chronological visual record.
The program began in January and was not initially disclosed to Baltimore’s mayor, city council or other elected officials. Now that it’s public, police say the plane will fly over the city again as a terrorism prevention tool when Fleet Week gets underway on Monday, as well as during the Baltimore Marathon on Oct. 15.
The logs show that the plane made flights ranging between one and five hours long in January and February, June, July and August. The flights stopped on Aug. 7, shortly before the program’s existence was revealed in an article by Bloomberg Businessweek.
The program drew harsh criticism from Baltimore residents, activists and civil liberties groups, who said it violates the privacy rights of an entire city’s people. The city council is planning to hold a hearing on the matter; the ACLU and some state lawmakers are considering introducing legislation to limit the kinds of surveillance programs police can utilize, and mandate public disclosure and discussion beforehand.
Baltimore has been at the epicenter of an evolving conversation about 20th century policing. Last spring, its streets exploded in civil unrest after a young black man’s neck was broken inside a police van.
Freddie Gray’s death added fuel to the national Black Lives Matter movement and exposed more problems in a police department that has been dysfunctional for decades. The department’s shortcomings and tendencies toward discrimination and abuse were later laid bare in a 164-page patterns and practices report by the U.S. Justice Department.
This is not the first time Baltimore has served as a testing ground for surveillance technology. Cell site simulators, also known as Stingray devices, were deployed in the city for years without search warrants to track the movements of suspects in criminal cases. The technology was kept secret under a non-disclosure agreement between the FBI and the police department that barred officers from disclosing any details, even to judges and defense attorneys. The Supreme Court recently ruled that warrantless stingray use is unconstitutional.”